Quad9 Cybersecurity Trends and Insights | May 2023
A Monthly Insight into Quad9’s Top Blocks
In December 2022, Quad9 published our first monthly, in-depth report exploring the trending DNS lookups of malicious hostnames we blocked the prior month. Each month, Quad9 users can download the entire report, which will provide a breakdown of several cybersecurity metrics, including but not limited to the prior month’s highest trending malware by volume of attempted domain access and type.
This information is valuable because it further sheds light on the most prominent malware, phishing, spyware, and botnet threats of which individuals and network administrators should be aware. For Quad9 users, the information in the monthly reports is more than supplemental intel surrounding trending cybersecurity and privacy threats. It also serves as additional peace of mind that Quad9’s public and free DNS service is helping to provide its users with a safer, more private online experience.
Quad9 Identified Cybersecurity Threat Trends – April 2023 Data
This month, Quad9 presents our overall top threats with regional activity information for the first time. In April 2023, we observed users in three regions mainly targeted with DDoS, crypto-miners, and Banking Trojans.
APAC and EMEA Regional Threats – April 2023 Data
During April 2023, the highest volume of queries initiated by users located in the Asia-Pacific (APAC) and Europe, the Middle East, and Africa (EMEA) regions was to the domain attributed to the Fodcha DDoS botnet.
Fodcha Command remains a relatively new yet powerful DDoS botnet, discovered by 360 Netlab researchers in April 2022. This DDoS botnet has caused quite a stir within the cybersecurity community, as researchers report the latest version has grown unprecedentedly.
Quad9 data confirms our suspicions that threat actors remain persistent in exploiting vulnerabilities for DDoS operations. Throughout April 2023, the volume of access attempts remains consistent. Furthermore, Quad9’s data suggests that attackers continue to be interested in supply chain vulnerabilities, which are difficult for users to identify and remediate. Notably, during April 2023, Singapore and Japan had the highest volume of queries to DDoS domains amongst users in the APAC region, while France and the Netherlands reported the most impacted users within the EMEA region.
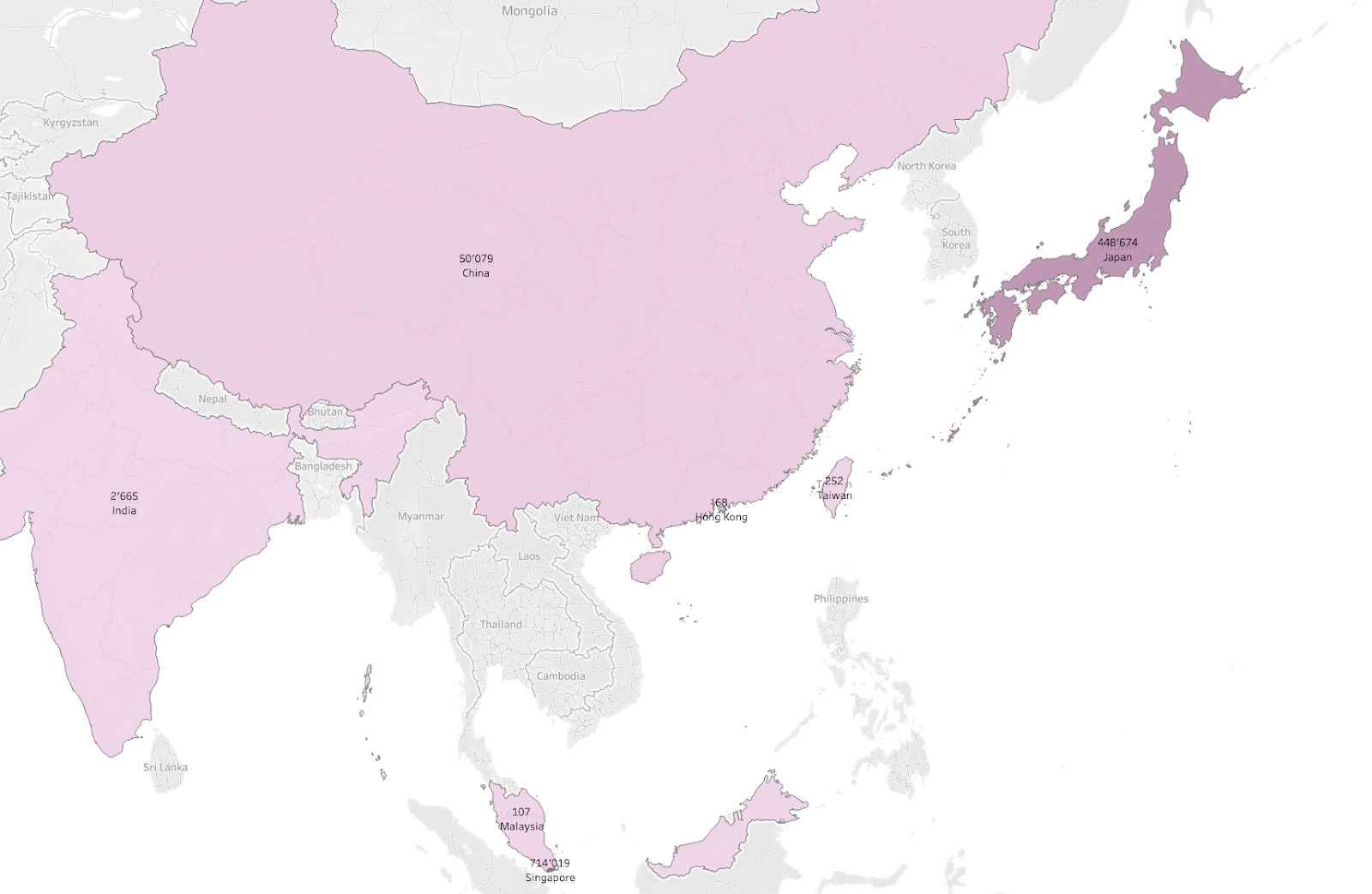
Source: quad9.net – April 2023 DDOS Volume APAC
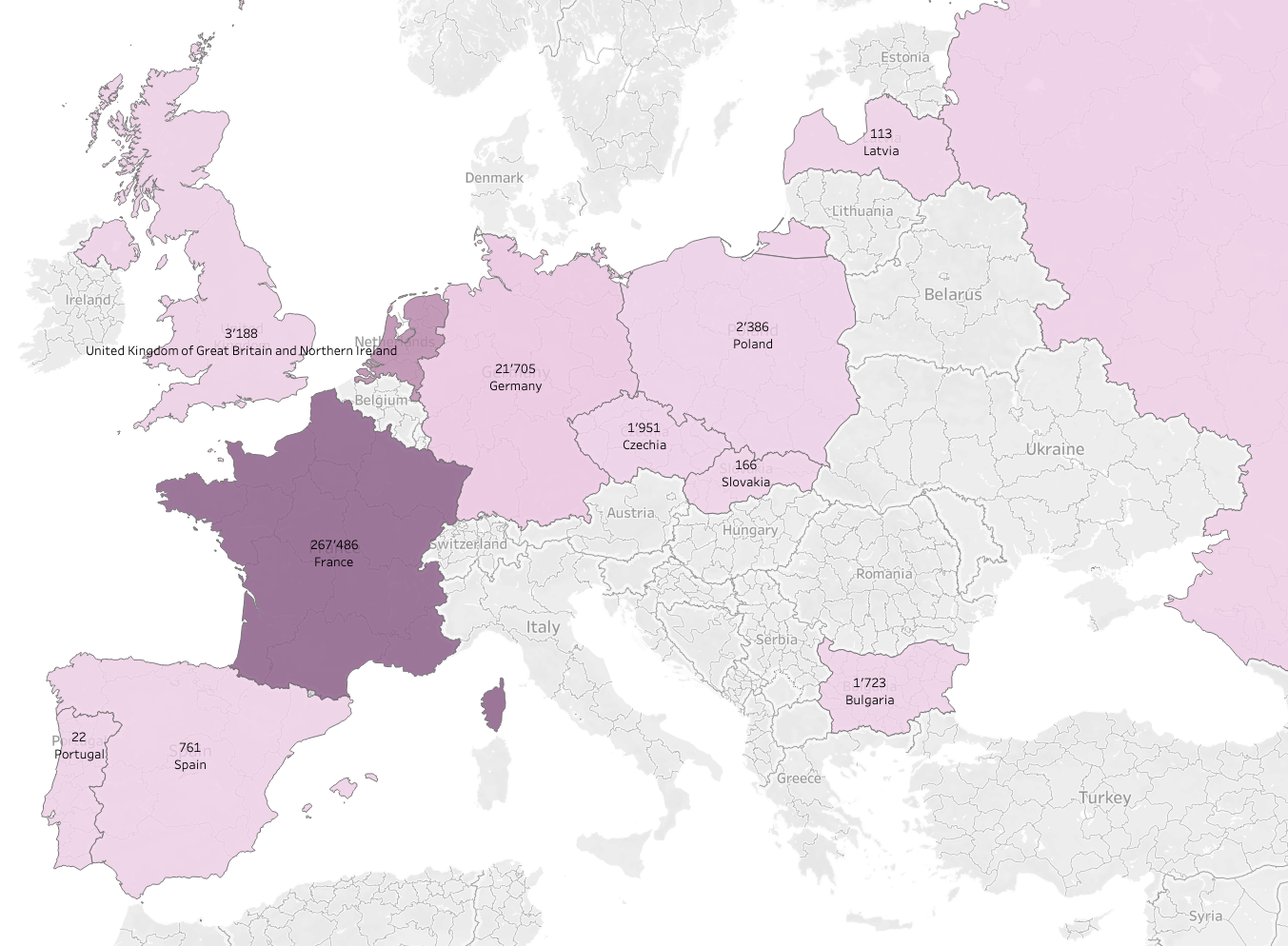
Source: quad9.net – April 2023 DDOS Volume EMEA
The Americas Regional Threats – April 2023 Data
For users in the Americas region, the highest volume of threats observed and blocked during April 2023 were attributed to crypto-mining domains and banking trojans.
Traditionally, cryptocurrency miners require significant system resources to maximize virtual currency output. As a result, threat actors attempt to exploit other users’ machines for mining purposes. Coin miners can originate from multiple channels, including, but not limited to, user-installed software to Trojan drops. According to Quad9’s telemetry data, the most impacted users for this threat type during April 2023 were located in the US.
The Ursnif/Gozi banking trojan was also among the top observed threats targeting users in the Americas during April 2023. Quad9 first observed queries to the domain attributed to the Gozi campaign in December 2022. Gozi (aka Ursnif) is spread through malspam with Microsoft Office document attachments or ZIP files. Ursnif is designed to collect victim information from cookies, login pages, and web forms.
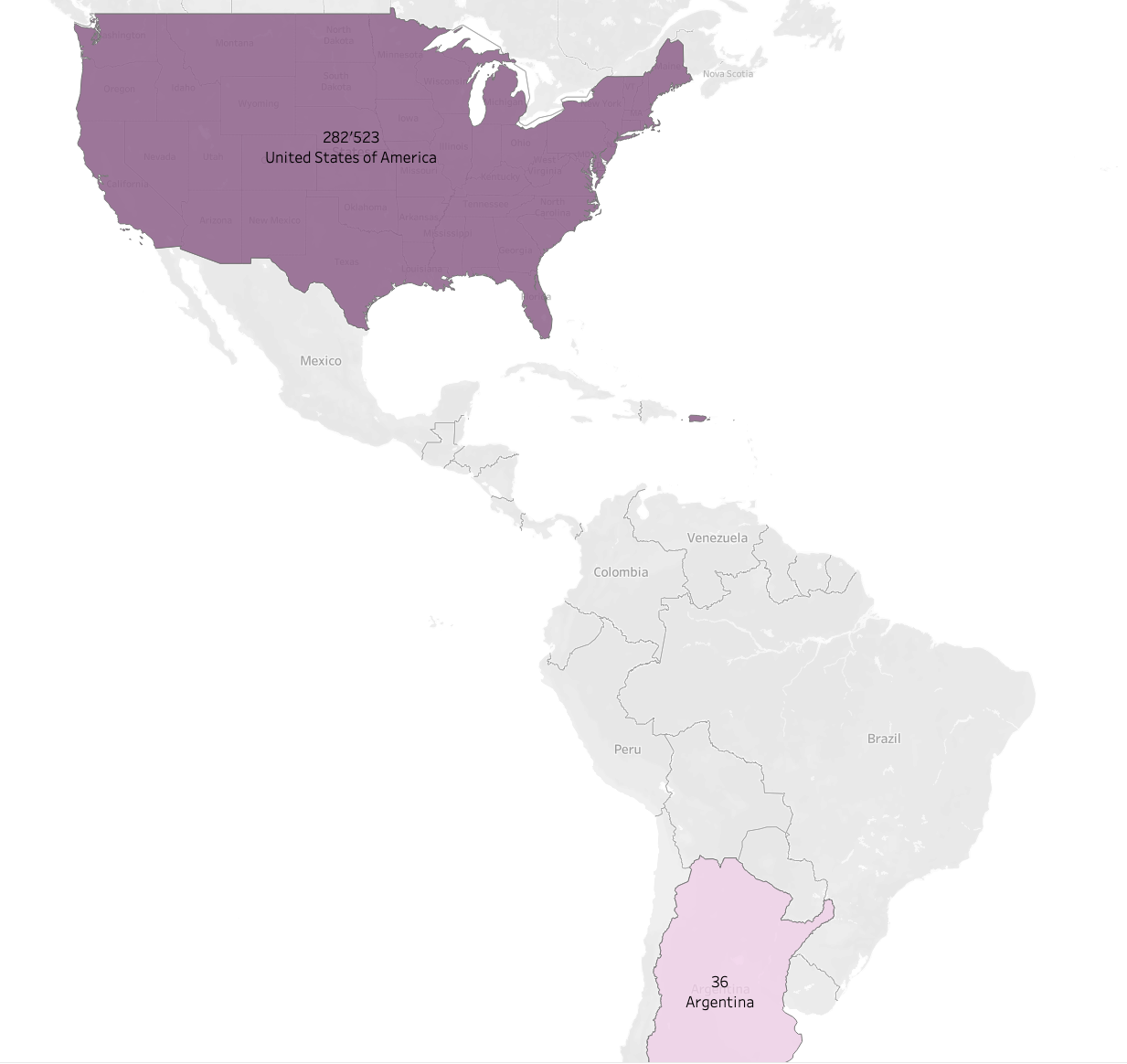
Source: quad9.net – April 2023 coin miner and banking trojan threat victimology
Global Cyber Threats Overview – April 2023
DDoS - During April 2023, the highest volume threat targeting global Quad9 users was attributed to DDoS. The domain which recorded the highest volume of DDoS traffic continued to be attributed to Fodcha Command and Control (C2) server. As mentioned above, APAC and EMEA were the regions with the highest volume of Fodcha Command queries.
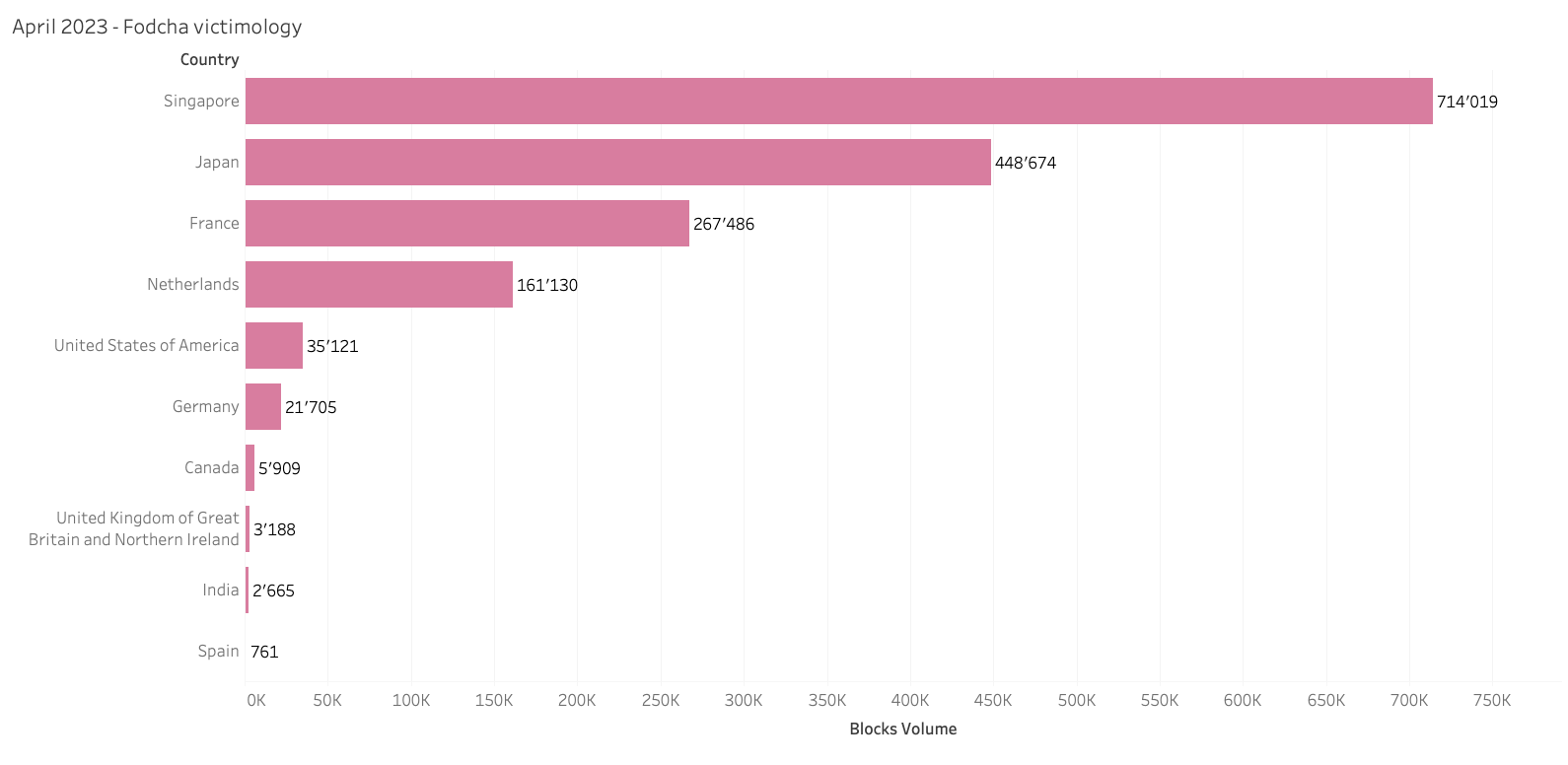
Source: quad9.net – April 2023 Fodcha breakdown by country
PixPirate– Brazilian Banking Trojan – _Another top threat observed targeting global Quad9 users during April 2023 was the Brazilian banking trojan, PixPirate. This new Android-based malware targets LATAM countries, specifically Brazil, which can be confirmed by Quad9 telemetry data, as seen below. The primary goal of this malware is to steal sensitive information to defraud users who regularly use the Pix platform. PixPirate masks itself with familiar names and icons, appearing to victims as a legitimate application.
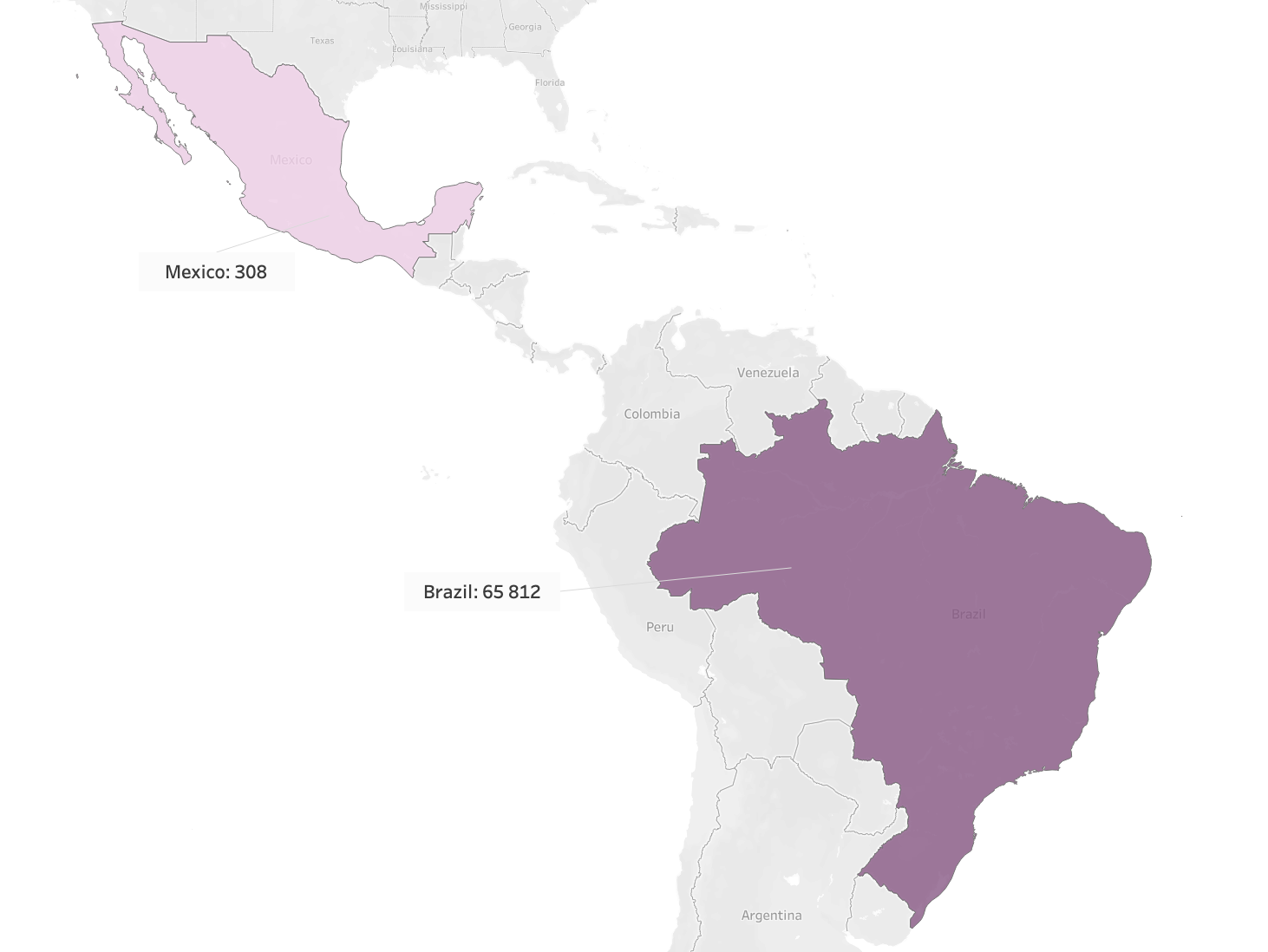
Source: quad9.net – April 2023 LATAM PixPirate Observations and Blocks by Quad9
_ViperSoftX Java Script Threat – _ViperSoftX is a multi-stage cryptocurrency stealer distributed through torrents and file-sharing sites. ViperSoftX was initially observed in 2020 and has grown extensively. Based on Quad9’s observations, this threat has recently been actively exploited. ViperSoftX is a Windows malware that deploys a Google Chrome extension named “VenomSoftX” [3]. Quad9 observed multiple domains generated using a domain generation algorithm (DGA) reported by threat researchers. During April 2023, victimology data shows that the most impacted users by ViperSoftX were in the US, Canada, and Germany.
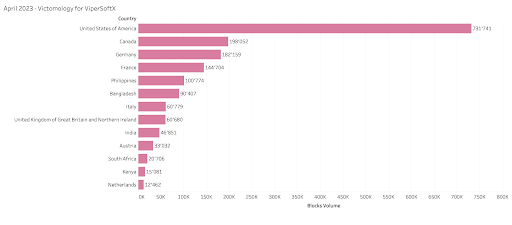
source: Quad9.net – April 2023 ViperSoftX Victimology
Dragon Breath APT – DLL Side-Loading – One of the top observed and blocked threats globally during April 2023 was attributed to the Dragon Breath APT campaign. This group of threat actors evolved their attacks, utilizing a double-clean-app technique and DLL side-loading to target the gambling and gaming industries. Attackers entice victims with _trojanized _versions of popular applications. Additionally, the group has added new layers of complexity to its attacks with the double DLL side-loading tactic, which allows them to evade detection. During April 2023, Quad9 users who were the most targeted by this campaign were in Indonesia, Iran, Japan, and the US.
The Takeaway
Quad9’s mission is to improve the security and stability of the Internet, creating an ecosystem where users are less vulnerable to risks and more effective in their daily online interactions. By preventing connections to known malicious sites, Quad9 reduces exposure risks before they are downloaded to a device or potential victims gain access to fraudulent websites.
Access the full April 2023 report
About Quad9
Quad9, a nonprofit in the US and Switzerland, provides free cybersecurity services to the emerging world via secure and private DNS lookup. Quad9 currently operates over 200 locations across more than 90 nations, blocking hundreds of millions of malware, phishing, and spyware events daily for millions of end users. Quad9 reduces harm in vulnerable regions, increases privacy against criminal or institutionalized interception of Internet data, and improves performance in under-served areas. Quad9 is a collaboration with Packet Clearing House (PCH), Global Cyber Alliance, and IBM.
References:
1. https://www.bleepingcomputer.com/news/security/fodcha-ddos-botnet-reaches-1tbps-in-power-injects-ransoms-in-packets/
2. https://www.cleafy.com/cleafy-labs/pixpirate-a-new-brazilian-banking-trojan
3. https://chris.partridge.tech/2022/evolution-of-vipersoftx-dga
4. https://www.hivepro.com/wp-content/uploads/2023/05/Dragon-Breath-APT-Evolves-with-Double-DLL-Sideloading_TA2023216.pdf